SECURITY Security Policy

Security Policy
Basic Policy
RONDHUIT Co., Ltd. (hereinafter referred to as "the Company") is committed to protecting the information assets entrusted to us by our customers from threats such as accidents, disasters, and crimes. To meet the trust of our customers and society, we will implement company-wide information security measures based on the following policies.
1. Establishment of Information Security Management System
To promote our efforts in information security, the Company will have its management take the lead in establishing necessary regulations. All employees will acquire the knowledge and skills required for information security and engage in security measures.
2. Compliance with Laws and Contracts
The Company will comply with laws, regulations, rules, and contractual obligations related to information security.
3. Collection of Technical and Security Information
We will strive to collect the latest technical and security information to adapt to new technologies and enhance security measures against emerging threats.
4. Education and Training
We will ensure that all employees are informed about this policy and related regulations, share the latest security information, and conduct regular training sessions.
5. Provision of Safe and Stable Services
By implementing information security measures at every stage of service development and operation, we aim to provide safe and stable services.
6. Risk Countermeasures
We will establish criteria for evaluating security risks and conduct regular assessments of the information assets we own and manage. Based on the evaluation results, we will implement necessary countermeasures.
7. Incident Response System
We remain vigilant against potential security incidents by pre-establishing response procedures for when incidents occur. In case of an incident, we will promptly follow these procedures and notify relevant parties. We will also analyze the incident's details to implement measures for prevention of recurrence.
Additionally, any violations of laws or contracts related to information security or accidents will be handled appropriately with efforts made to prevent recurrence.
8. Management of Outsourcing Partners
When outsourcing business operations, we will appropriately manage and supervise partners through confidentiality agreements, commitments to understand and comply with our information security policies, regular education, etc., ensuring they maintain a security level equivalent to ours.
9. Inspections and Audits
We will conduct regular internal audits related to information security to ensure reliable efforts in information security and continuous improvement.
10. Changes to Information Security Policy and Notification
The Company may change this information security policy. Any changes will be communicated to users via our website, email, or other appropriate methods.
Information Security Management Items
- Confidentiality
- Establish procedures for adding, changing, or deleting accounts and execute them according to approval flows.
- Prevent unauthorized logins through login management.
- Detect and prevent unauthorized communications or authentication requests from various logs.
- Ensure access rights to various system resources are properly set and maintained.
- Monitor for vulnerabilities in equipment, firmware, operating systems, middleware, applications, and address them through correction procedures or approval flows when discovered.
- Monitor operational status of equipment, firmware, operating systems, middleware, applications, and address attacks according to response procedures or approval flows when detected.
- Integrity
- Define procedures for system changes and execute them according to steps, verification, and approval flows.
- Establish update procedures for manuals, checklists, approval flows, etc., managing history during updates.
- Create configuration information documents, requirement specifications, manuals, managing history during updates.
- Perform regular multi-generational data backups for recovery in case of data corruption.
- Implement appropriate account management and access control.
- Maintain highly confidential information through encryption or equivalent methods.
- Availability
- Identify normality and abnormality in services.
- Individually monitor equipment, firmware, operating systems, middleware, applications.
- Ensure that equipment constituting services is configured redundantly or equivalent methods (backup & restore) are functioning.
- Prepare response procedures and systems for handling system failures.
Incident Response System
1. Responsible Persons/Organizations
In case of an information security incident at the company:
(1) Administrator Oversees important decisions regarding incidents; managed by the CEO.
(2) System Personnel Handles incident reception and various segmentation tasks; managed by the Product Manager.
(3) Employees Engage in detection, investigation, response; handled by the DevOps team.
(4) External Organizations Engage in detection, investigation, response; handled by cloud vendors or development contractors.
(5) Related Parties Include customers, users, police, security agencies.
2. Contact Methods for Users
3. Service Failure Flow
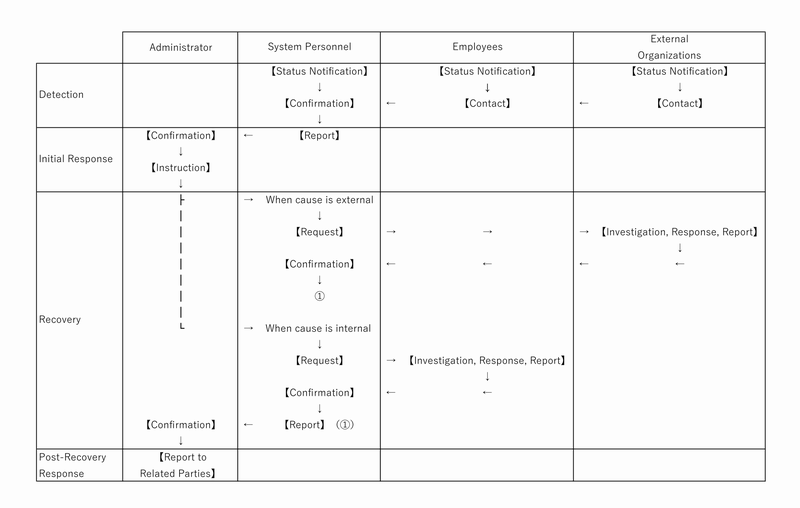
The flow for responding to service stoppages or data loss due to cloud infrastructure service outages or internet connection failures is as follows:
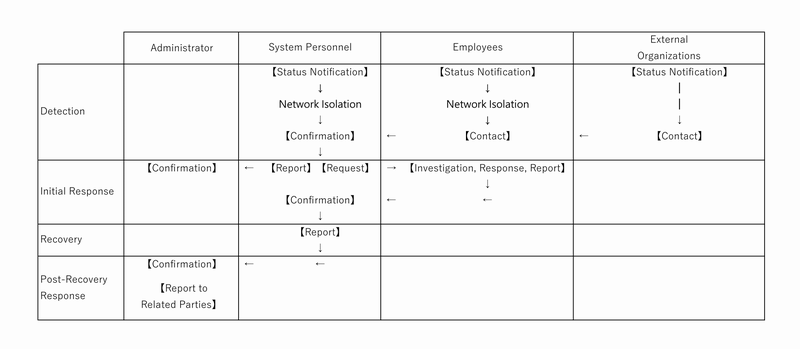
4. Attack on Service Flow
The flow for responding to attacks on services due to unauthorized access or data tampering/encryption is as follows:
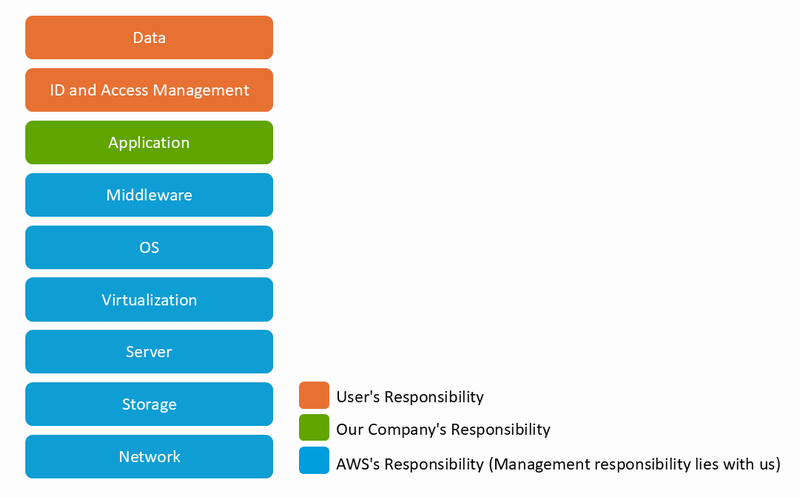
Shared Responsibility Model in SaaS
Our company provides KandaSearch as a SaaS using Amazon Web Services as IaaS.
Therefore, we define the shared responsibility model in SaaS as follows: